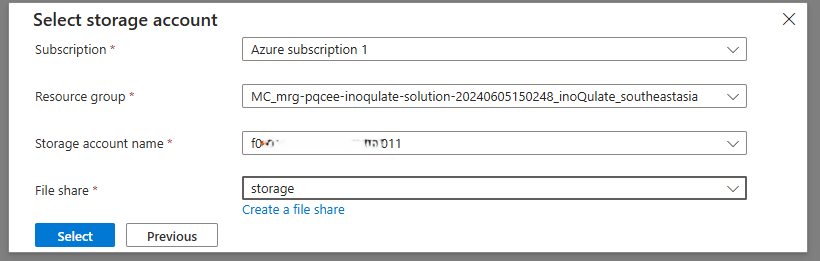
1.3. Set up the Solution¶
After completing the steps in Subscribe to inoQulate from the Azure Marketplace, the deployment should complete in about 20 minutes.
1.3.2. Download and install setup files¶
In your terminal, run the following commands.
Note
If using your own Bash terminal, please change directory to the
configdirectory inside your mount point instead.cd clouddrive/config curl -O https://raw.githubusercontent.com/pqcee/public/38dd8b77caa47348667b668c99bd9a9b4fdb5c0f/inoQulate-v1.2.0-config.zip unzip inoQulate-v1.2.0-config.zip
If there are no errors, continue by running.
./setup.sh
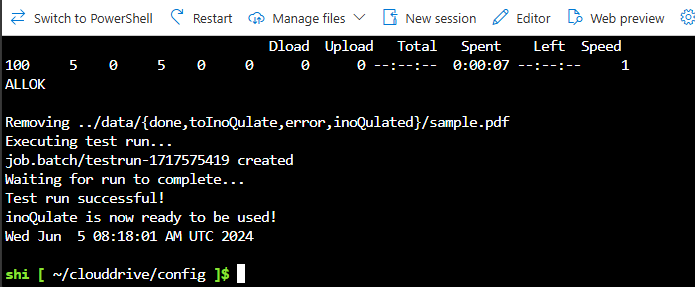
Allow about 20 minutes for the setup to complete. The console output is also written to
log.txtin the same directory. If you encounter any issues with the setup, download and includeconfig/log.txtfrom the File Share in your support request.The installation completed successfully when you see the message:
inoQulate is now ready to be used!
1.3.3. Install the inoQulate PDF Verifier¶
The inoQulate PDF Verifier installer is available for the Windows platform. The installer is included in the File Share.
1.3.3.1. Download from the Azure Cloud Shell¶
Download the installer directly from your Azure Cloud Shell.
In the Azure Cloud Shell panel, click Manage Files and then Download.
Paste the following text in the required field.
clouddrive/config/inoQulate.PDF.Verifier_1.0.0_x64_en-US.msi
Click the notification to download the file.
1.3.3.2. Download from the Azure Portal¶
Download the installer from the Azure Portal.
On the Azure Portal, access the File Share page.
On the left panel, click Browse.
Click the
configdirectory.Click
inoQulate.PDF.Verifier_1.0.0_x64_en-US.msi.Click Download.
1.3.3.3. Install the verifier¶
Run the
inoQulate.PDF.Verifier_1.0.0_x64_en-US.msithe installer. You need administrative privilege to run the installer.Go through the installer wizard to the Completed page by clicking Next and Install. You do not need to change any settings in the wizard.
Uncheck Launch inoQulate PDF Verifier.
Click Finish.