2. Using the PacketQC solution¶
2.1. TL;DR¶
This section covers a quick guide on how to use PacketQC if you wish to jump right in and start using.
Perform the following steps to generate a security report with PacketQC:
Once you have the PacketQC website open, select the input box in the center of the screen or the browse button. This will pull up a File Upload dialog.
Then, either double click the pcap file you wish to upload, or select the preferred pcap file once and select Open on the bottom right of the dialog.
Finally, click on the Generate Security Report button to generate the security report. Waiting time for report generation is around 10s - 180s depending on size of pcap file. Maximum accepted size for the pcap file is 20MB.
Once the report is generated, a multi-tab report will be generated showing a dashboard of graphs, and the security report. By default, the dashboard is selected and shown:
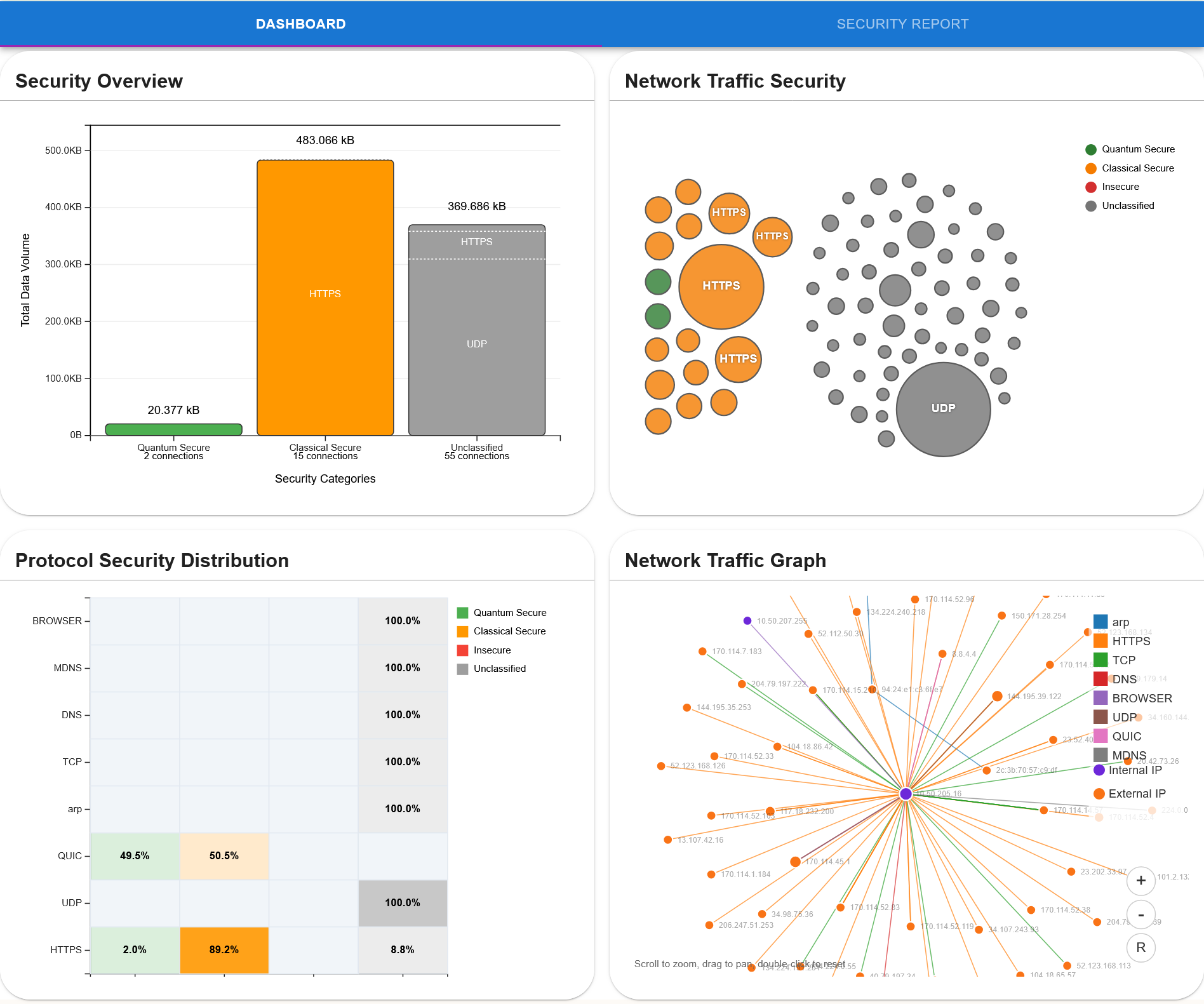
The dashboard currently consists of four graphs:
Security Overview (Bar Chart)
Network Traffic Security (Bubble Graph)
Protocol Security Distribution (Heatmap)
Network Traffic Graph
The Security Overview and Network Traffic Security graphs will show the general quantum secure posture of the network, while the Protocol Security Distribution and Network Traffic graphs show the more minute details of the network topology.
To get a more detailed view of the connections in the network, select the SECURITY REPORT tab and you will be able to see the following:
All Protocols tab on the Sidebar, shown on the left, will be selected by default. The other tabs will show colouring based on the security level of the protocol and port combination. The legend for the security level colours is shown in the bottom right of the page, in the footer.
All connections will be shown on the right. To filter by protocol and port, select one of the other tabs in the Sidebar. This will show all the filtered connections for the selected protocol. To filter by port, select the arrow icon to deploy the dropdown which will show the port tabs, then select one of the port tabs.
If you want to more details about the connection, select the dropdown button, to the right of the connection card. The dropdown will show details such as the key exchange and encryption algorithms for the particular protocol.
2.2. PacketQC Filter connections by protocol and port feature¶
This section covers how to filter the connections shown in the security report by protocol and port combinations.
When a packet capture is scanned with PacketQC, the connections are grouped by transport protocols and low-level protocols (like ARP and ICMP). Then all other protocols that run over specific ports over the transport protocols are grouped together, as children to the transport protocol. An example of this show in the image below:
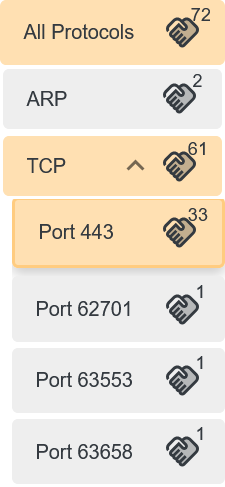
When one the parent sidebar tabs are clicked, only the connections for the protocol are shown. To expand the parent tab, click on the arrow icon. Clicking on the child tabs will filter out the connections of the transport protocol for the port shown on the tab.
2.3. PacketQC Security Classification of Connections, Protocols and Ports feature¶
This section covers how the network security of the connections, as well as the protocol:port combinations are classified.
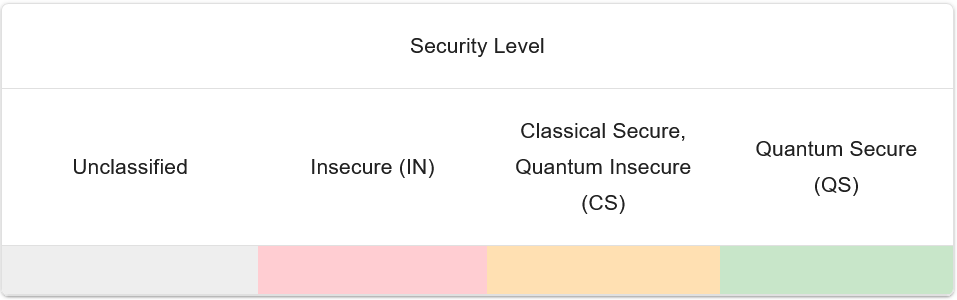
The network security of the connections are defined using 3 security levels (from top to bottom, worst to best):
Unclassified
Indicates that the security level of the connection is not known, usually because the connection lacks any cryptographic layer running over it.
Shown as light grey.
Insecure (IN)
Indicates that the connection is not secure against classical computer attacks or quantum computer attacks.
Shown as light red.
Classical Secure, Quantum Insecure (CS)
Indicates that the connection is secure against classical computer attacks, but not secure against quantum computing attacks.
Shown as light orange.
Quantum Secure (QS)
Indicates that the connection is secure against both classical computer attacks and quantum computer attacks.
Shown as light green.
A legend table is shown on the right of the footer and the bottom of the PacketQC webpage for you to refer to, as shown in the image below:
The security level is shown at the connection level in the security report as shown below:
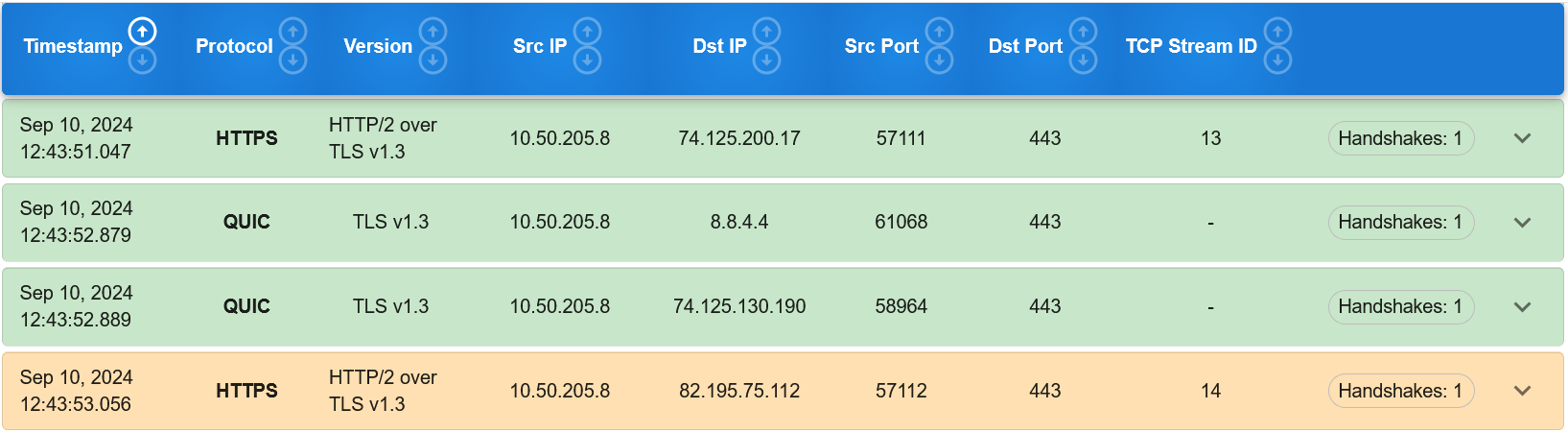
From the image above, we can see that there are 3 quantum secure connections and 1 classically secure connection based on the 3 connections being light green and the one connection being light orange.
At the protocol:port level on the Sidebar, the weakest security colour of all the connections in each protocol:port combination is set to each tab as shown in the image below:

This is to provide at a first glance, which protocol:port bindings are quantum secure and which are not, providing an easy way to quickly filter and find the weak ports and connections running over those protocol:port bindings.
2.4. PacketQC Sort by column feature¶
PacketQC also offers sorting by column, where you can click any column, and the connections shown will automatically be sorted in ascending order. This is indicated by the white up arrow as shown in the image below:

To sort the column in descending order, simply click the same column again, which will turn the up arrow grey and the down arrow white, indicating that the connections are now sorted in descending order:

By default, the connections shown are sorted by Timestamp in ascending order as shown in the image below:
When another sidebar tab is clicked or a new report is generated, the sort will revert back to sort by Timestamp, in ascending order, if another column was selected previously.
2.5. PacketQC Analysis of common security protocols features¶
Section 2.5. covers the Analysis of common security protocols features by PacketQC.
As mentioned in section 1.2., PacketQC supports the analysis of the following four common network security protocols:
TLS
QUIC
IPsec
SSH
RDP
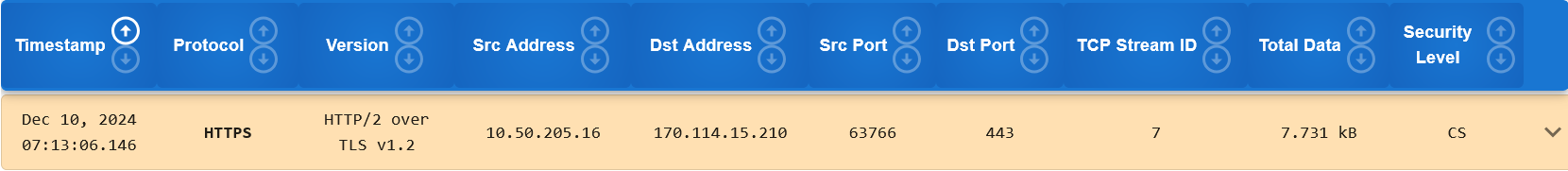
PacketQC shows the following attributes for analysis of all the supported network security protocols:
Timestamp (shown in UTC)
Protocol
Version (of Protocol)
Src Address (IP/MAC)
Dst Address (IP/MAC)
Src Port (number)
Dst Port (number)
TCP Stream ID
Total Data (in bytes)
Security Level
Here is a sample of this is displayed by PacketQC:
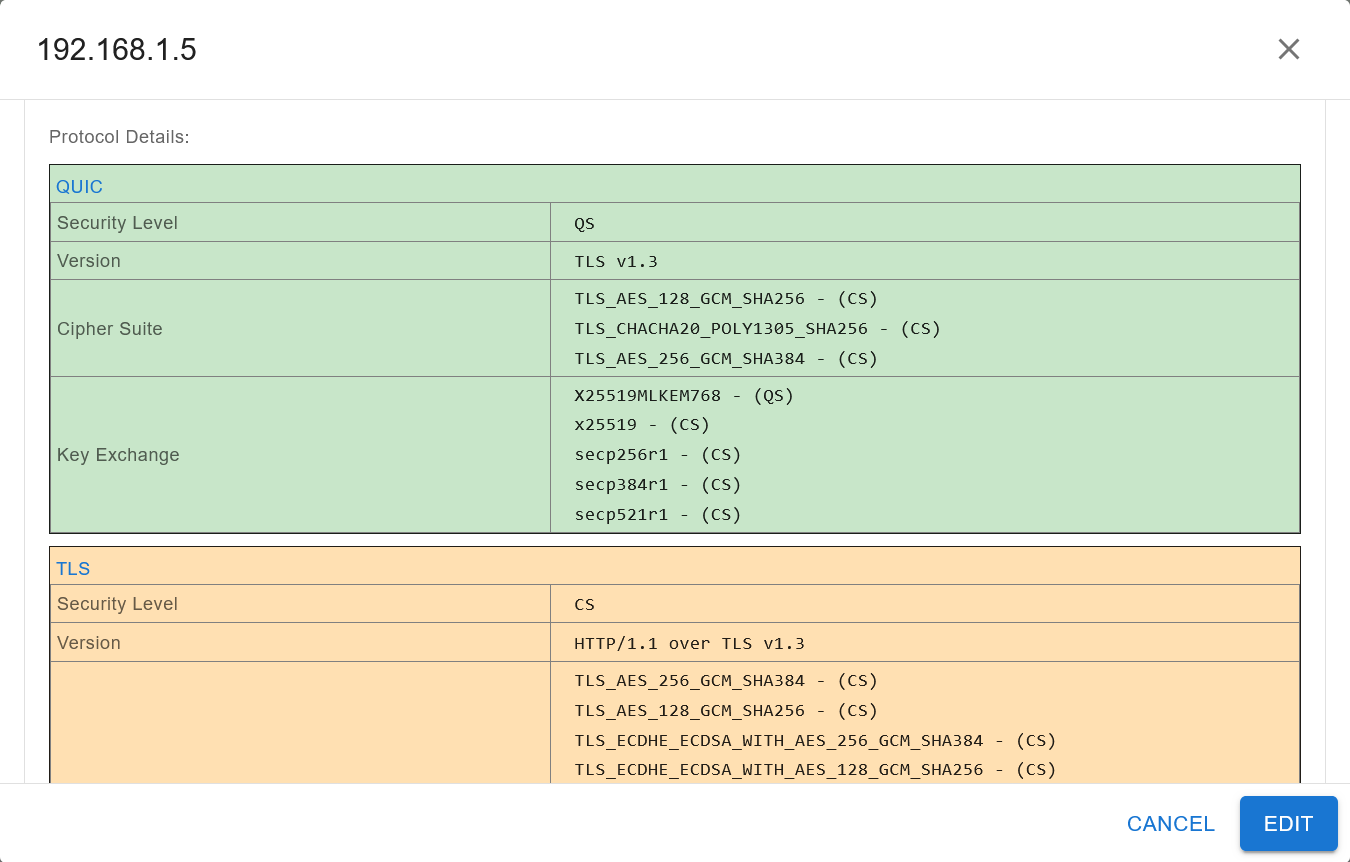
At the right side of the card header, is an arrow icon pointing downward. Clicking on it will cause the arrow to point upwards and simultaneously, show a dropdown below that specific row. The dropdown shows a detailed view of the cryptographic protocol for the connection.
In the following subsections, we will go over the detailed views for each of supported network security protocols shown at the start of this section.
2.5.1. Detailed View of TLS and QUIC¶
The detailed view of TLS shows a ClientHello card on the left of the dropdown and a ServerHello card on the right of the dropdown. Above both cards, lies a header that provides the number of TLS handshakes that have occurred for this connection. An example partial detailed view is shown below:
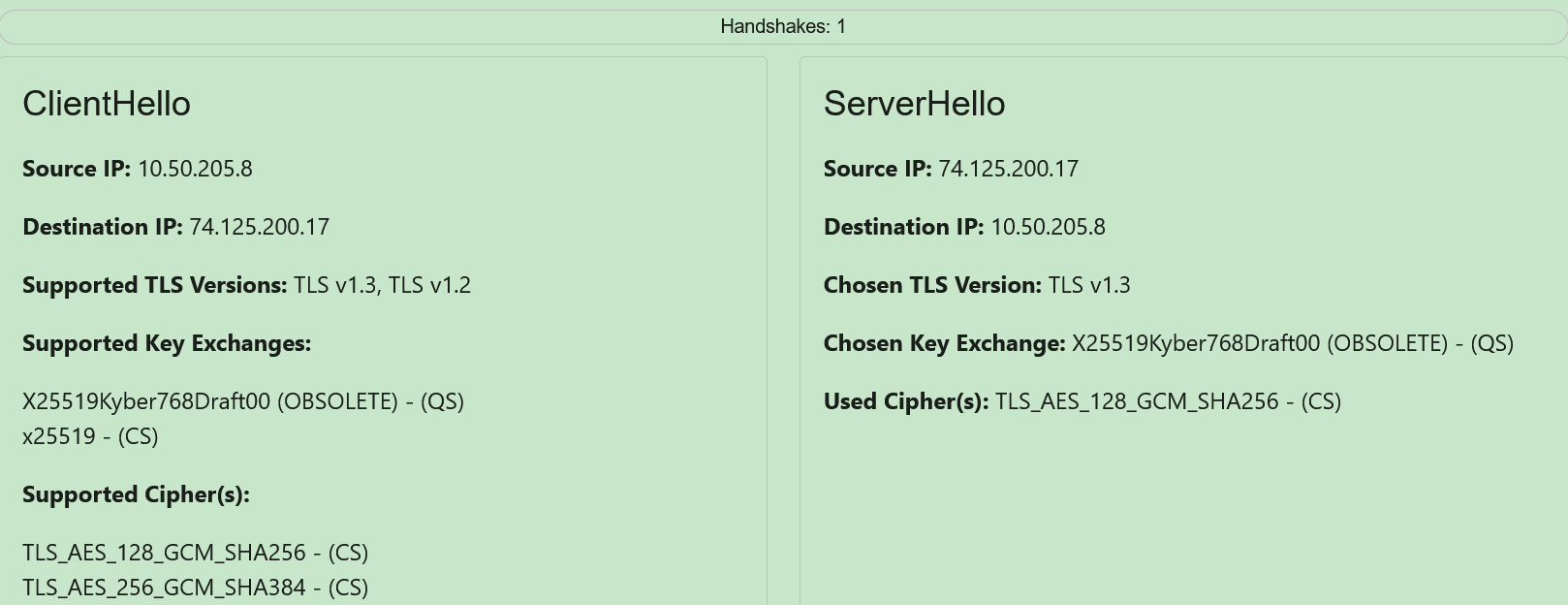
Both the ClientHello and ServerHello have Source IP and Destination IP fields. The difference lies in order of the IP addresses shown. In the ClientHello, which is the client to server part of a TLS/QUIC connection, the client IP is shown as the Source IP and the server IP is shown as the Destination IP typically. In the ServerHello, the opposite is true, as it is the server to client part of a TLS/QUIC connection. An example of this dichotomy is shown below:
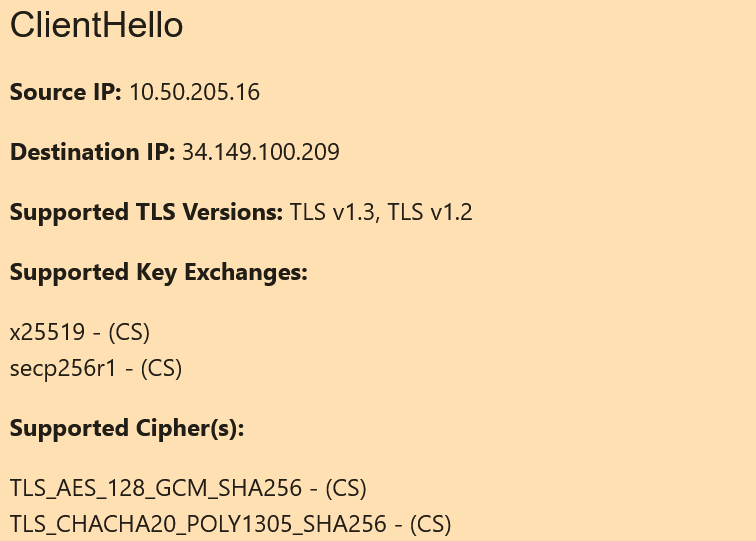
The ClientHello also has 3 other fields:
Supported TLS Versions
This is a single line containing all the versions of TLS that the client supports.
Supported Key Exchanges (Only for TLS v1.2 and below)
This is a vertical list of all the key exchange algorithms supported by the client.
Supported Ciphers
This is a vertical list of all the cipher suites supported by the client.
Cipher suites are strings that contain a combination of an encryption algorithm (like AES-256) and a hash algorithm (like SHA-384).
As previously mentioned, for TLS versions 1.2 and below, the cipher suites also have the key exchange algorithm in the string (like ECDHE).
A partial ClientHello card is shown below:
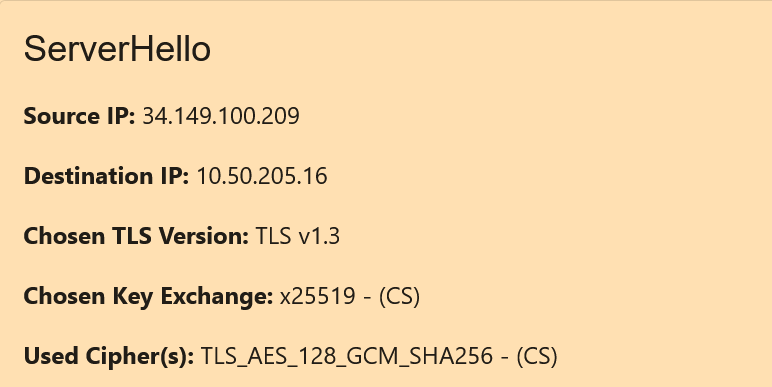
The ServerHello, on the other hand, has 2 or 3 other fields shown (based on the version of TLS v1.3), that mirror the 2 or 3 fields shown in the ClientHello:
Chosen TLS Version
This is the TLS Version chosen by the server for use in the connection between the client and server.
Chosen Key Exchange (Only for TLS v1.3)
This is the key exchange algorithm chosen by the server for use in the connection between the client and server.
Due to the architecture of TLS v1.3, only TLS v1.3 has a separate Chosen Key Exchange.
Due to the architecture of QUIC (QUIC only uses the latest version of TLS, which is TLS v1.3), the ServerHello card for a QUIC connection will always have a Chosen Key Exchange.
Used Cipher
This is the cipher suite used by the server for the connection between the client and server.
For TLS v1.2 and below, the key exchange algorithm is included in the cipher, along with encryption and hash algorithms.
On the other hand, due to the architecture of TLS v1.3, TLS v1.3 has a separate Used Cipher field and Chosen Key Exchange field.
Similarly, due to the architecture of QUIC (QUIC only uses the latest version of TLS, which is TLS v1.3), the ServerHello card for a QUIC connection will always have a Used Cipher field and a Chosen Key Exchange field.
A sample ServerHello card (using TLS v1.3) is shown below:
2.5.2. Detailed view of IPsec¶
The detailed view for IPsec consists of header containing the number of Handshakes for the IPsec connection as well as four algorithm fields and an optional Other timestamps (UTC) field, containing a vertical list of timestamps, which is shown if there is more than one handshake. The four algorithms shown differ based on IPsec version.
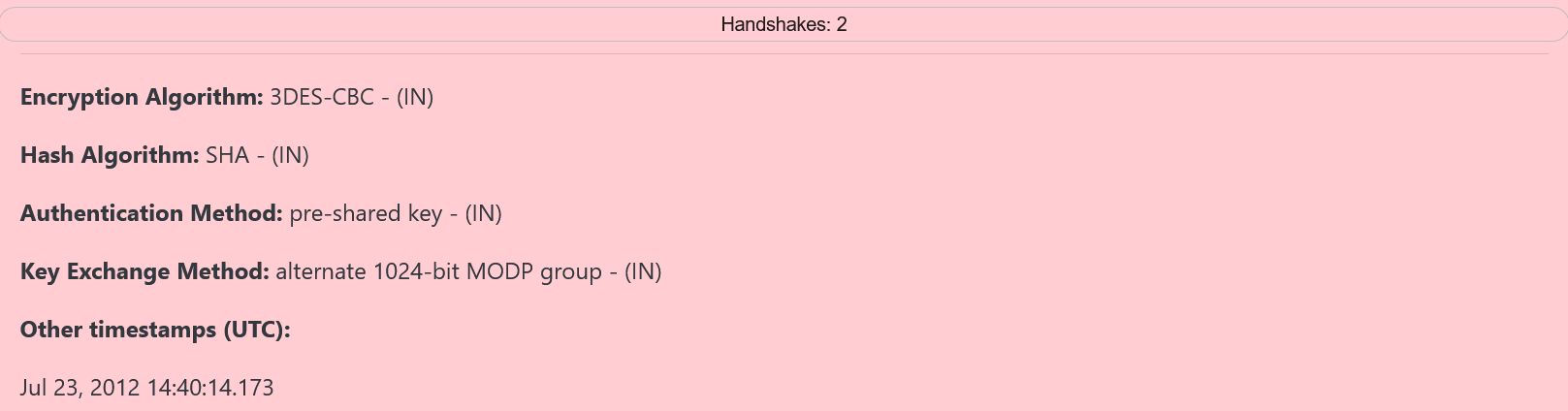
IPsec IKEv1 contains the following 4 algorithms:
Encryption Algorithm
Hash Algorithm
Authentication Method
Key Exchange Method
An example of an IPsec IKEv1 detailed view is shown below:
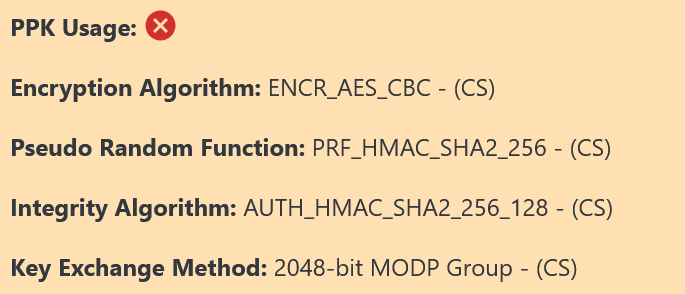
IPsec IKEv2, on the other hand, contains 5 fields:
PPK Usage
Encryption Algorithm
Pseudo Random Function
Integrity Algorithm
Key Exchange Method
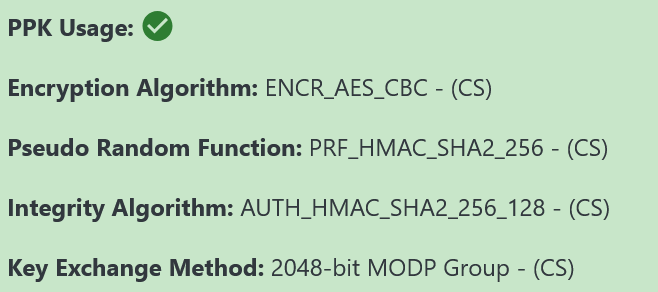
The PPK Usage field will either show a red cross or green tick icon, indicating the use of PPK (Post-quantum Preshared Key) in the connection and not, respectively. The usage of PPK for the IPsec connection is a direct indicator of the quantum security for the connection.
An example of an IPsec IKEv2 without PPK connection’s detailed view is shown below:
And an example of an IPsec IKEv2 with PPK connection’s detailed view is shown below:
2.5.3. Detailed view of SSH¶
The detailed view for SSH consists of a total of 8 algorithms, split up into 2 sections.
The first section contains the following algorithms:
Key Exchange Algorithm
Server Host Key Algorithm
The second section which is directly below the first section, is split into 2 columns. The first column contains the algorithms for traffic going from client to server. The second column contains the algorithms for traffic going from the server to the client. In both cases, the 3 algorithms shown in each column are:
Encryption algorithm
MAC algorithm
Compression algorithm
A sample SSH detailed view is shown below:
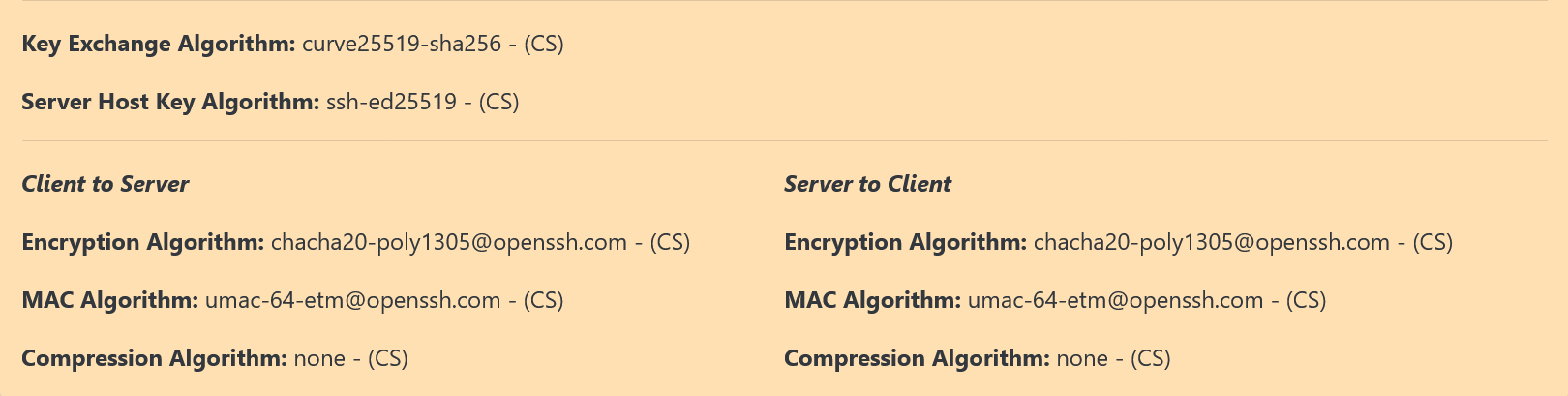
2.5.4. Detailed view of RDP¶
The detailed view for RDP consists of just two fields:
Encryption Method - shows the type of RC4 encryption used
Encrytion Level - shows the level of RC4 encryption Used
A sample RDP view is shown below:

2.7. PacketQC Download Report feature¶
This section covers the Download Report feature.
As mentioned in the previous section (2.6), to access this feature, you must first upgrade.
PacketQC contains a Download Network Report button that when clicked, will produce a .json file containing the network report. For this to work, the network report must first be generated.
The feature is still under development, and the structure of the report has yet to be finalised.
2.8. PacketQC Asset Tracking feature¶
This section covers the Asset Tracking feature.
As mentioned in section 2.6, to access this feature, you must first upgrade.
To see the Asset List tab, first generate a network report. Then click on the Asset List tab, to see the Asset Management view:
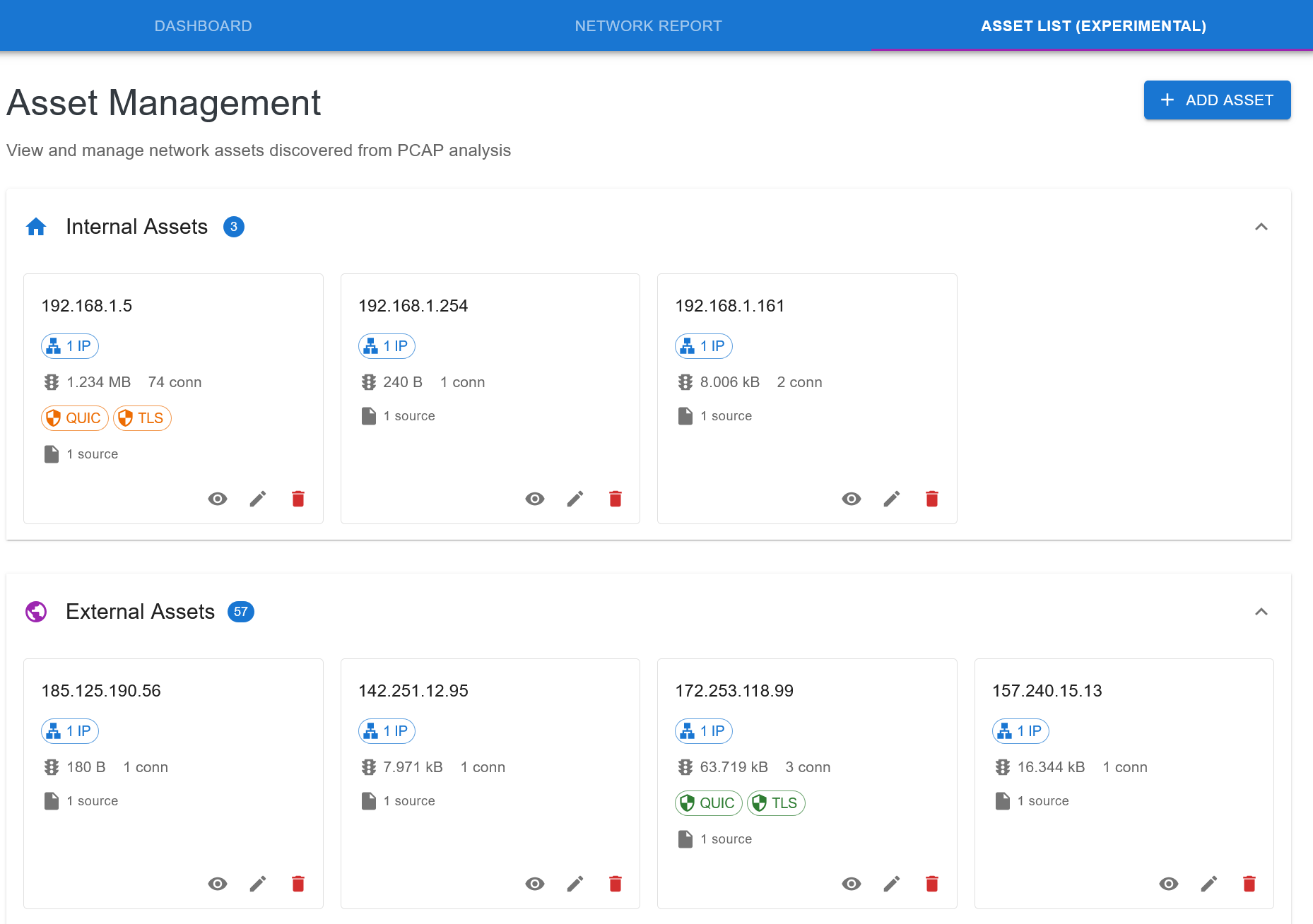
The view provides several features including:
Adding and removing assets
An accordion with separation between internal and external assets
An overview of each asset containing: - asset name or IP address (if no asset name) - number of IP addresses tagged to the asset - total amount of traffic recorded as passing through the asset across all its IPs - number of connections associated with the asset - any analyzed crypto protocols captured in the IPs tagged to the asset - CBOM uploaded to the asset - Number of pcap file sources for the asset
There are 3 modes for each asset: view, edit and delete.
To enter view mode, simply click on the eye icon on the bottom-right corner of an asset card. This will open up a dialog with 3 tabs:

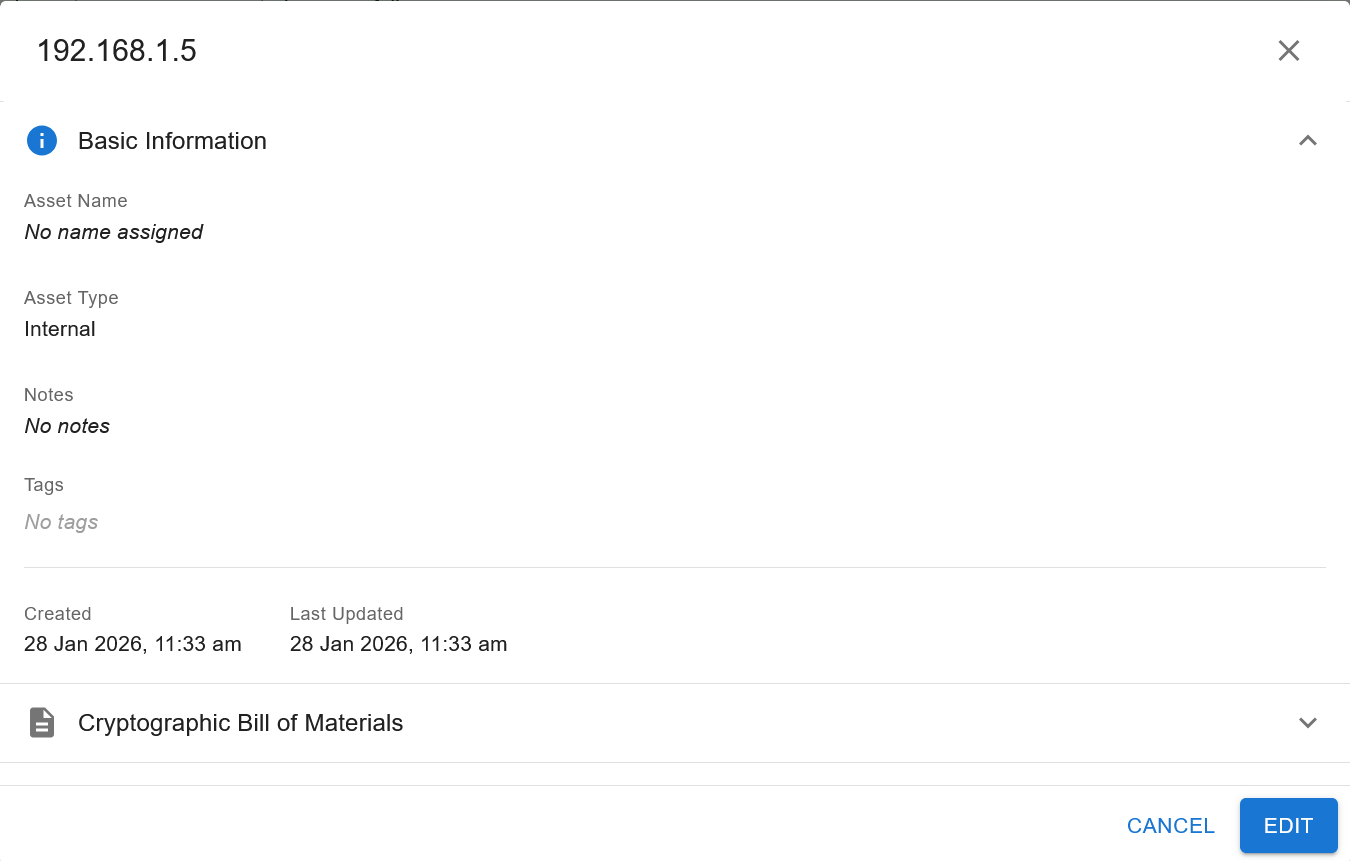
2.8.1. Asset Basic Information Tab¶
The Basic Information tab contains the following 6 properties:
Asset Name
Asset Type
Notes
Tags
Created
Last Updated
The first 4 of the above properties (Asset Name, Asset Type, Notes and Tags) can be edited in edit mode. Created contains the timestamp of asset creation. Last Updated will contain the same timestamp as Created on asset creation, but will update whenever you modify the asset in edit mode.
2.8.2. Asset Cryptographic Bill of Materials Tab¶
The Cryptographic Bill of Materials tab will initially contain an empty prompt box as shown below:
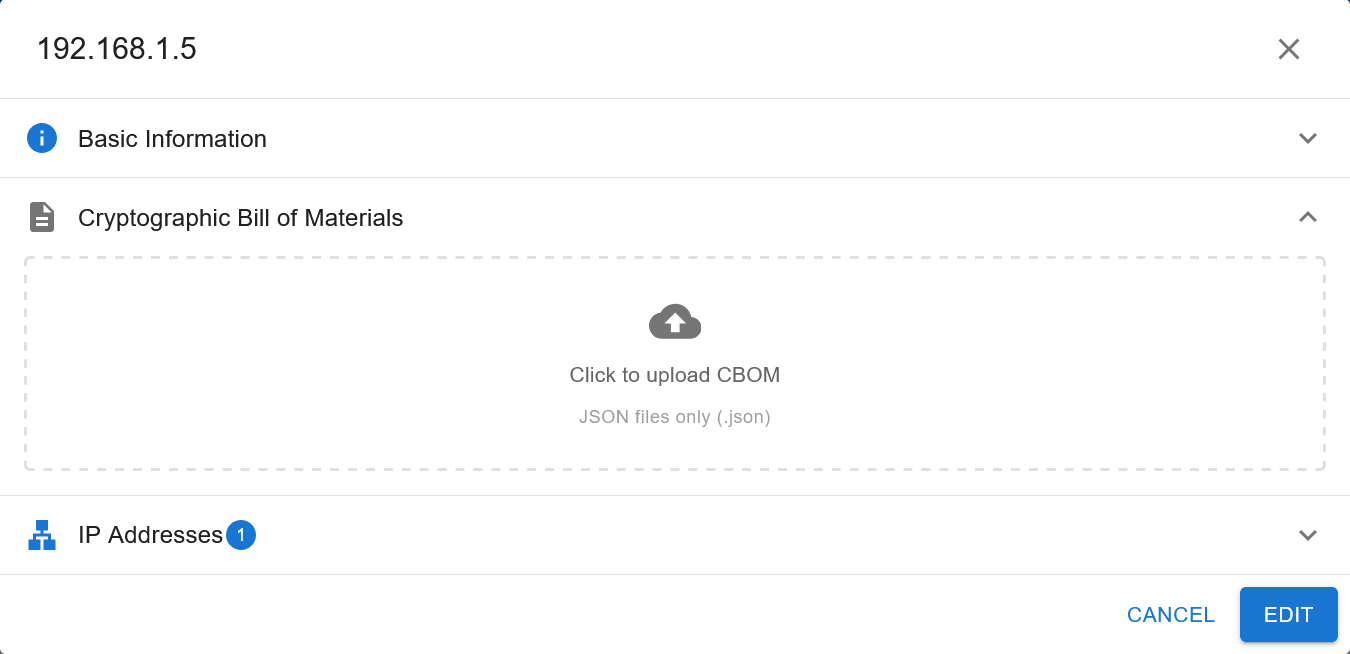
Click on the prompt box and upload the CBOM. To generate the CBOM, use IBM’s cbomkit-theia tool <https://github.com/cbomkit/cbomkit-theia>_.
Once uploaded, the CBOM will be processed and you will be able to see an analysis of the CBOM in the CBOM tab as shown below:
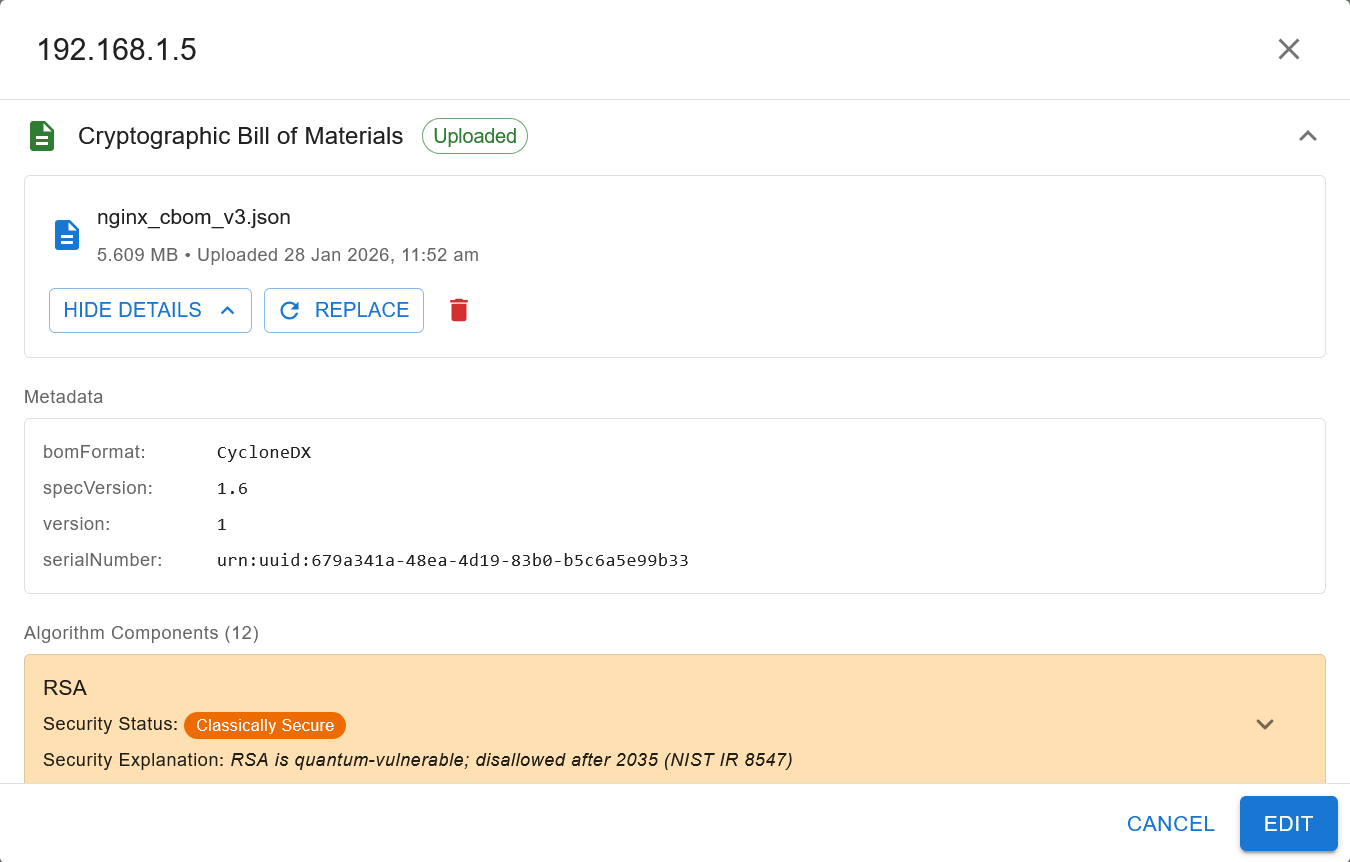
The view contains:
a header with basic details about the CBOM, and options to hide the details, replace the CBOM and delete the CBOM for the asset.
metadata section containing details about CBOM format and version.
a detailed breakdown of all the algorithm components found in the CBOM and whether they are quantum secure, classically secure or insecure as shown in the image below:
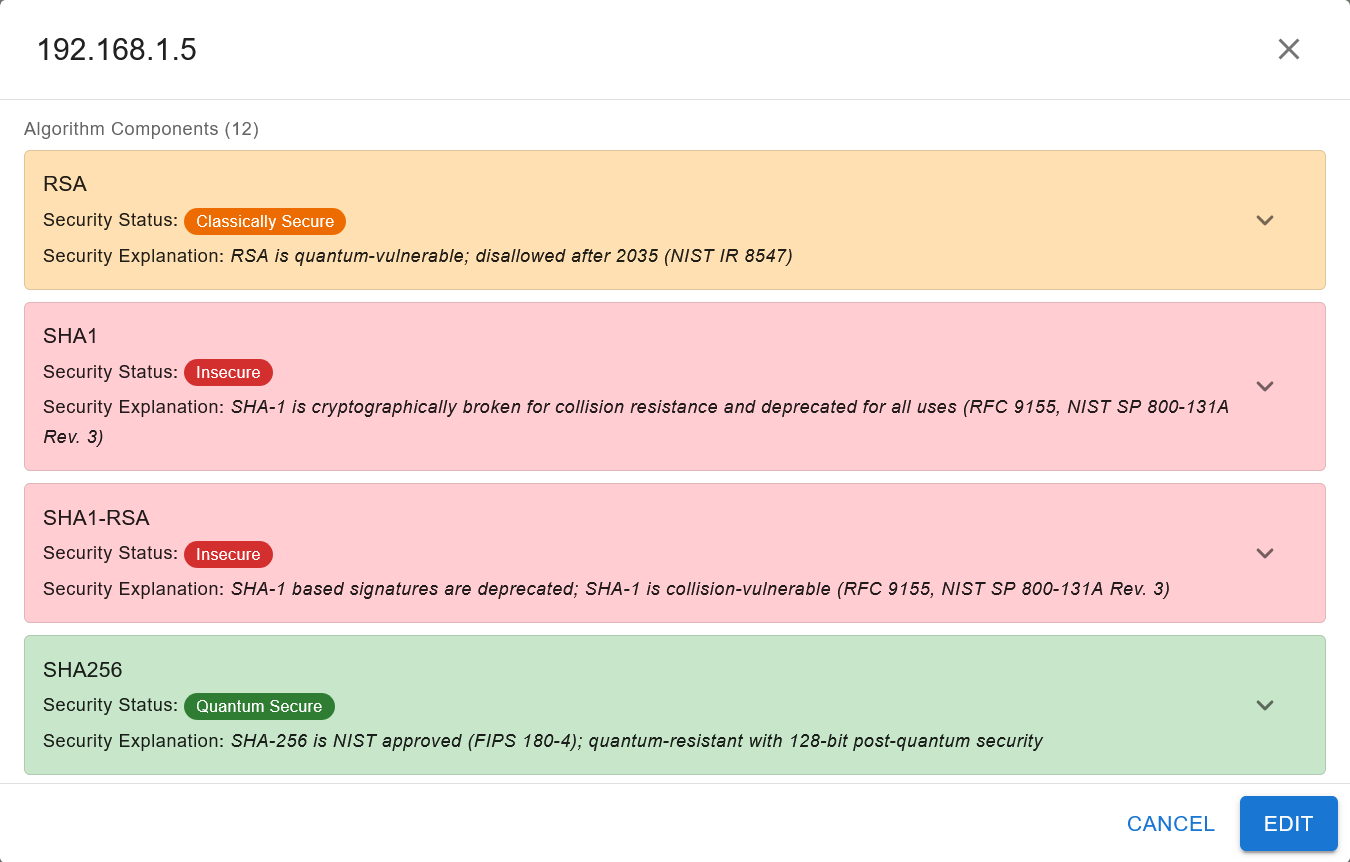
To investigate further, you may click on the downward pointing arrow on the right of the algorithm component, which will expand the following menu:
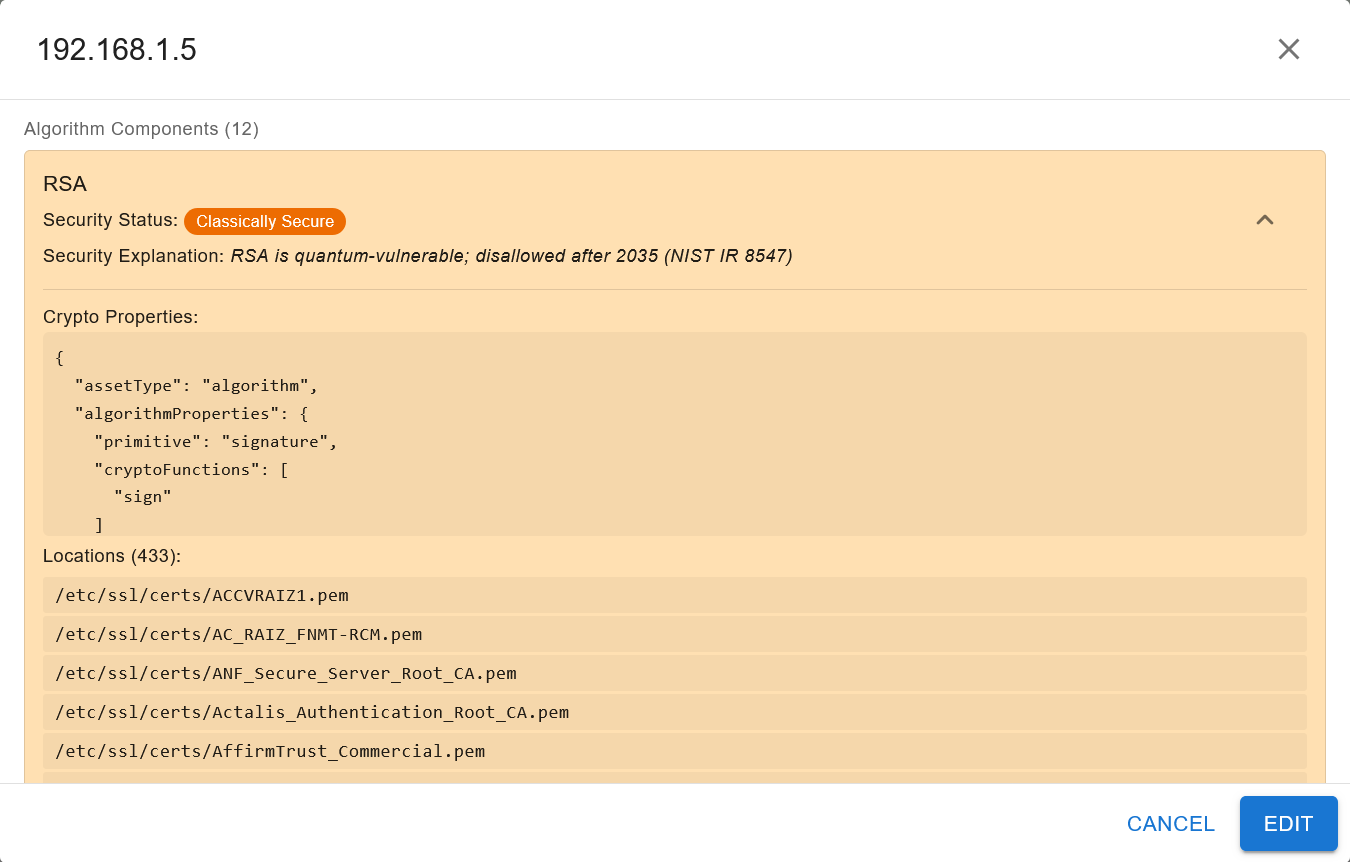
The expanded view will show: - the crypto properties of the algorithm (retrieved from the CBOM) - the location(s) of where the algorithm was located in the filesystem of the image or repository you scanned
In addition to algorithm components, a list of dependencies captured in the CBOM are also shown for completeness.
2.8.3. Asset IP Addresses Tab¶
The IP Addresses tab contains metadata surrounding the IP in question such as:
traffic load
number of connections
number of connected IPs
date of discovery
source pcap file
Which can be seen in the image below:
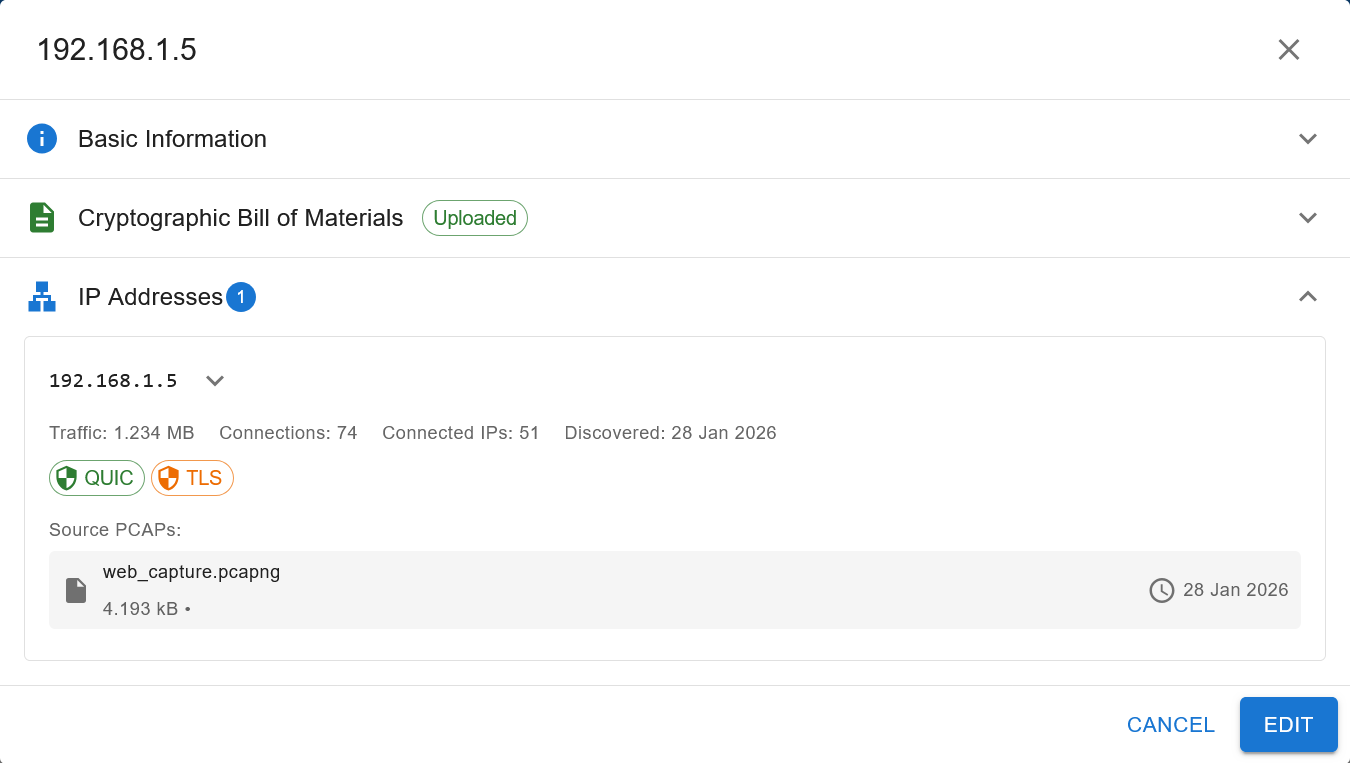
When you click on the down pointing icon to the right of the IP address, you will get an expanded view with more details such as:
a vertical list of all the connected IPs
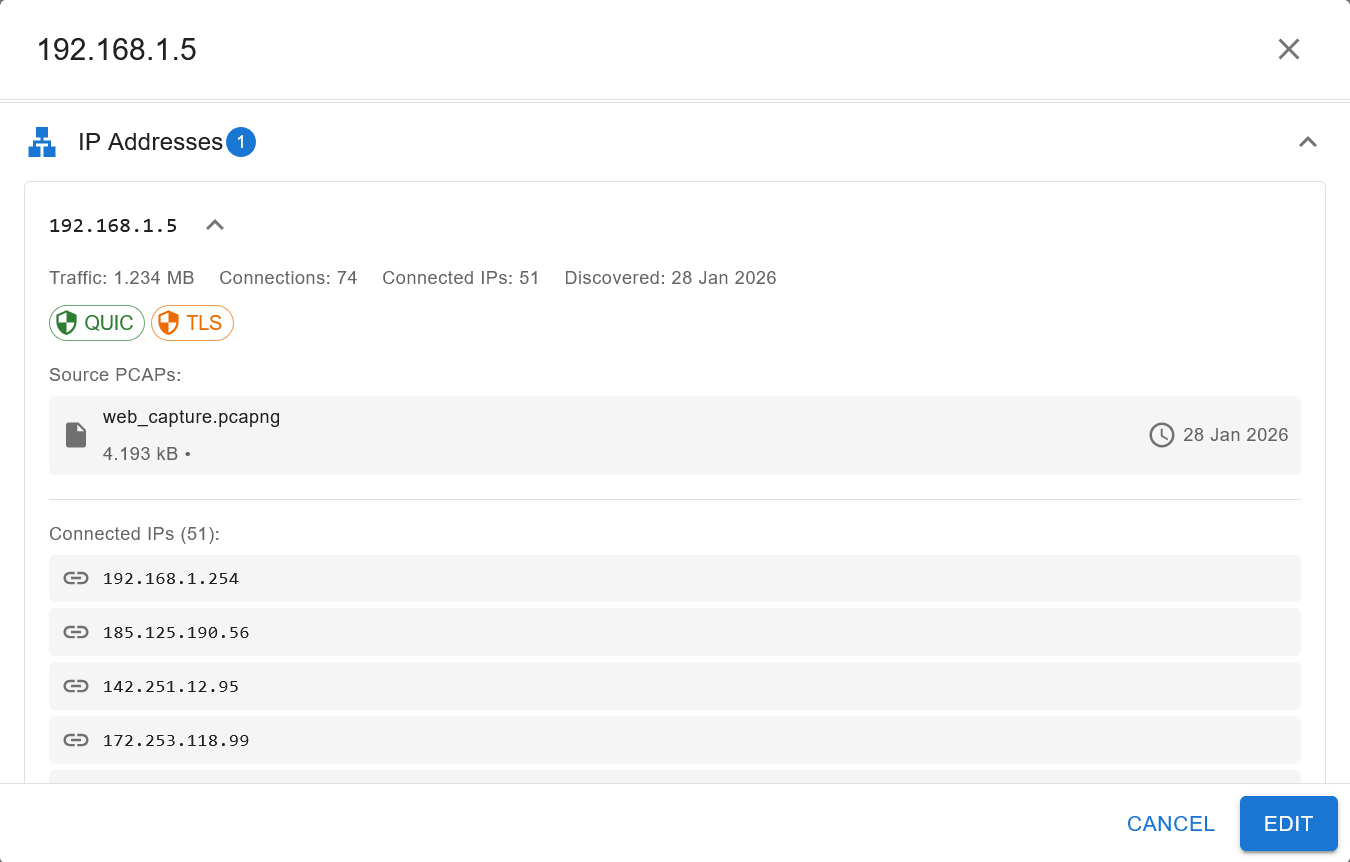
all the crypto protocol details across all connections to/from the IP address.