1. Getting started with PacketQC¶
This section covers all you need to know about PacketQC before you starting using it.
1.1. Before you start¶
Ensure that you have access to a browser and have the latest version of Google Chrome, Mozilla Firefox or Microsoft Edge.
- Ensure that you have at least one pcap file to use in the tool. The following formats have been tested and are supported:
.pcap
.pcapng
.cap
To capture a pcap file, we recommend you use either tcpdump or Wireshark.
Make sure to enter the correct website: https://packetqc.pqcee.com.
1.1.1. How to capture pcap¶
Wireshark¶
To capture in Wireshark, install and open it.
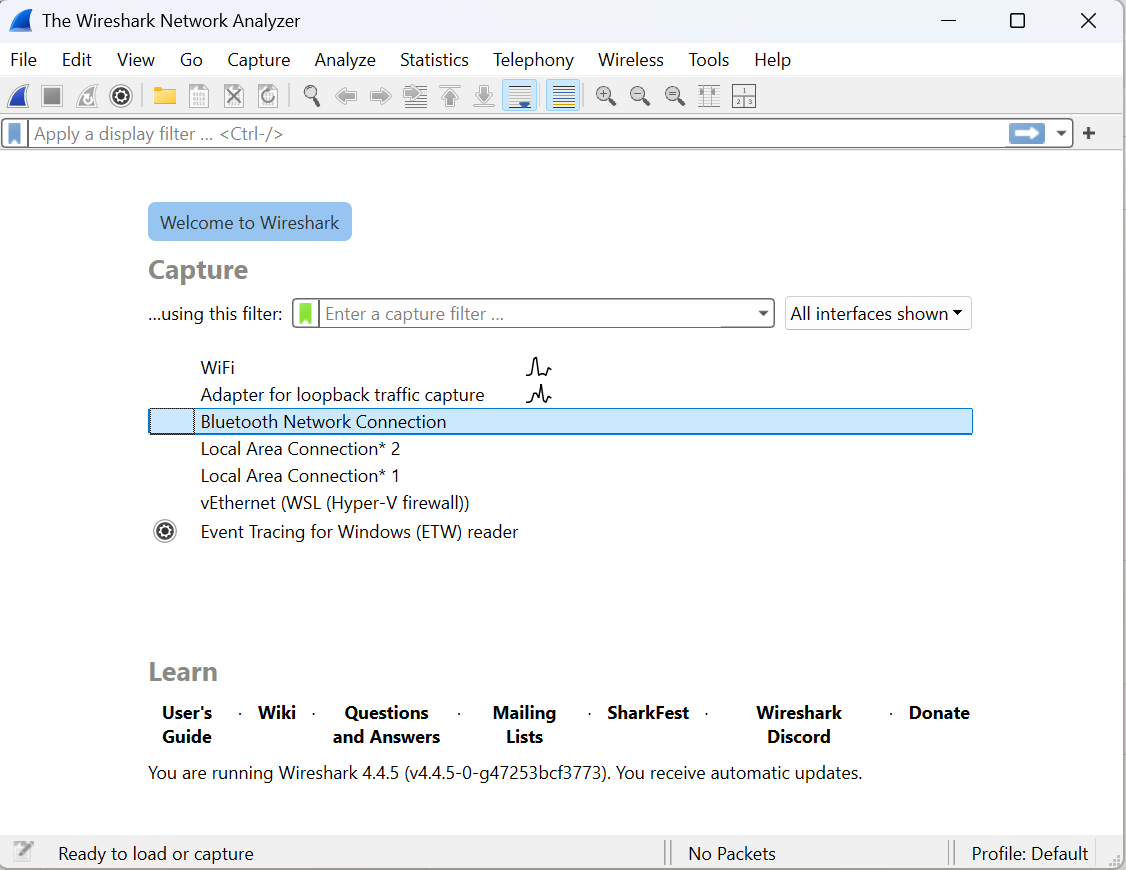
Then, select the interface you want to capture over, then click on the blue ‘fin’ button on the top left.
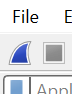
This will start capture. Once you are done capturing, click the red square button on the top left to stop capture.
Then, go to File -> Save or Save As, to save the capture. Select the file extension as .pcap or .pcapng.
Note
Only .pcap and .pcapng file extensions are accepted in PacketQC.
tcpdump¶
Use the following command to start capturing using tcpdump:
tcpdump -i eth0 -w capture.pcap
For more information on how to use tcpdump, look here: tcpdump Man Page.
1.2. PacketQC’s features¶
- PacketQC has several features:
Ability to get general network security posture from the dashboard.
Ability to filter connections by protocol and / or port.
Ability to sort connections by column.
Ability to classify security of individual interactions, as well as protocol and port combinations.
Analysis of common security protocols, including showing common attributes for each connection like timestamp and source IP address, and providing a detailed view as a dropdown for all the analyzed cryptographic protocols.
Ability to download security report in .json format. (Currently under development)
Ability to track assets (Currently under development)
Ability to upload and analyze Cryptographic Bill of Materials (CBOM)
- PacketQC is currently able to analyze the following cryptographic protocols (which cover the bulk of all encrypted traffic on the internet) for quantum and classical security:
TLS (Transport Layer Security)
QUIC (Quick UDP Internet Connections)
IPsec (Internet Protocol security)
SSH (Secure Shell)
RDP (Remote Desktop Protocol)
In addition to this, PacketQC shows whether individual algorithms are quantum secure (protected against quantum computing attacks), classically secure (protected against classical computing attacks) or insecure (not protected against both).
PacketQC is also able to scan and show all other non-crypto connections as well, although these connections are left unclassified.